Improving quality of indicators of compromise using STIX graphs
This paper addresses this issue by presenting a method to enhance the IoC quality through a knowledge graph and by establishing a threat score standard. The proposed method enriches intelligence by associating and merging different OSINT sources for a single IoC, following the 18 STIX Domain Objects (SDOs) (OASIS, 2023) dictated by the STIX Heuristic evaluation method.
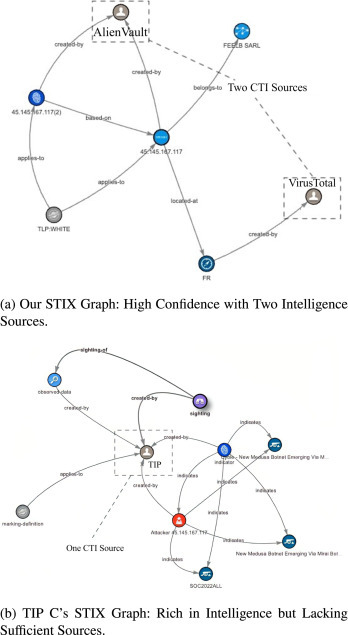
Fig. 11. Comparative analysis of confidence scores for IoCs.
Technology Overview
Improved IoC management by assessing threat severity and confidence scores. Used STIX graph-based approach to aggregate threat intelligence from various sources. Optimized IoC scoring on relevance, completeness, accuracy, timeliness, consistency.
Applications & Benefits
We developed a method to improve IoC value using CTI, significantly boosting threat data quality. This enhancement is achieved by integrating a multidimensional analysis framework that incorporates not only the volume and variety of data sources but also the contextual depth and temporal relevance of the information, thereby delivering a more nuanced and comprehensive understanding of cyber threats. We introduced the first IoC-specific severity and confidence scoring system, marking a 25.18% average confidence score variation from other platforms. We validated our approach within OpenCTI through Emotet and Medusa case studies, proving its effectiveness in creating detailed, actionable IoCs.
Abstract:
Cybersecurity relies on Indicators of Compromise (IoCs) to detect and address threats. Although Threat Intelligence Platforms (TIPs) and Open Source Intelligence (OSINT) are common sources for gathering IoCs, their reliability varies. In our study, we enhance the management of IoCs and OSINT by introducing a novel method that reliably assesses IoC’s threat severity and confidence scores, focusing on Structured Threat Information eXpression (STIX) for threat associations. Our approach, implemented on OpenCTI, significantly enhances IoC value, as it aggregates threat intelligence from diverse sources utilizing a STIX graph-based approach, which is a unique feature among TIPs. Additionally, our method employs heuristic analysis to optimize IoC scoring. It takes into account factors such as relevance, completeness, timeliness, accuracy, and consistency while emphasizing the confidence of the source. Notably, the proposed method has enhanced the precision of the confidence score, achieving a 25.18% reduction in the average difference of confidence scores compared to the benchmarked platform. The Emotet and Medusa case studies underscore the importance of source credibility in confidence scores, emphasizing our TIP’s precision in cybersecurity threat assessment and defense enhancement.

Improving quality of indicators of compromise using STIX graphs
Author:Sheng-Shan Chen, Ren-Hung Hwang, Asad Ali, Ying-Dar Lin, Yu-Chih Wei, Tun-Wen Pai
Year:2024
Source publication:Computers & Security Volume 144, September 2024
Subfield Highest percentage:99% Law #7 / 1105
https://www.sciencedirect.com/science/article/pii/S0167404824002773